Convenience or Compliance: The Critical Need for Data Ethics and Secure Electronics Disposal in the 21st Century
By Chiman Lee, CEWS
Data ethics is an increasingly relevant issue facing today’s businesses as modern technology snowballs. Organizations of all sizes face the challenging governance of unprecedented levels of electronic devices and the data contained therein. This electronic phenomenon is responsible for a relatively new branch of ethics emerging, data ethics. Data ethics covers the moral issues involved in possessing data, from creation to recording and destruction.
We’ll look at key considerations to keep in mind and understand why it is essential to incorporate data ethics and learn the advantages of discarding electronic data properly. By using standardized and certified methods, rather than taking haphazard approaches or being unknowingly careless about something that directly impacts personal privacy and our environment, we can all do our part to help protect people and, ultimately, our planet.
 DEFINING DATA ETHICS
DEFINING DATA ETHICS
As covered in a paper from Oxford Internet Institute1, data ethics refers to evaluating moral problems relating to data to formulate and support “morally good solutions.”
“Generation, recording, curation, processing, dissemination, sharing and use), algorithms(including artificial intelligence, artificial agents, machine learning and robots) and corresponding practices (including responsible innovation, programming, hacking and professional codes).”
Data ethics is a necessary, comprehensive study due to the industry’s speed of evolution and innovation. Researchers must try to remain two steps ahead as they develop secure and sustainable guidelines for data security that meet data ethics requirements both in the lab and in the field. The alternative to lack of proper data ethics meansanyone’s electronic data could be subject to abuse, monetization, or worse, whether known or not2.
RECOGNIZING VULNERABILITIES
Although big tech companies such as social media and search engine giants actively use customer data, claiming the collection is for consumer benefit, they are no less exempt from practicing data ethics. While the average consumer may be completely unaware of how much data is being captured (and its use case), it is reasonable that businesses should pursue best data ethics practices. Data is a powerful magnet, with the internet becoming our critical interface for conducting business at all levels.
For example, the Google search engine is now the data collection behemoth with 4.3 billion users worldwide3 (based on 4.72 billion internet users worldwide and a market share of 92.24%). Google’s search engine converts search results, ads displayed, and more based on a user’s account summary4. Facebook uses data to determine who you might know, track the websites you visit, and improve facial recognition. Things get more dubious when other add-on third parties enter the data gathering mission in exchange for services but are less transparent. For most consumers, unless they take deliberate steps to stay off-grid or secure their data, their data is being used for various purposes.
Hackers are constantly seeking data vulnerabilities and will most often target a business entity rather than trying to go after individuals for data exploits. Businesses often lack preparation, falling prey to hacks or ransomware that result in a data security breach, compromising their consumers’ data and trust. Data breaches exposed 36 billion records5 in the first half of 2020, a continually rising statistic.
SEEKING OUT THE INFORMED
Some small to mid-size companies are not up-to-speed with how many vulnerabilities they create when trying to secure sensitive data. On average, only 5% of companies’ folders have proper protection6. Businesses running an online marketplace are likely to team up with multiple third-party programs to handle the checkout, sales, and shipping. But each of those add-on services you incorporate is another potential weakness because you have no control over their levels of security. Are businesses safer because they are enterprise corporations, or more dangerous because they are targeted more often by hackers?
For most companies, outsourcing to data security experts and getting personal consultations based on their business needs will be the way to go. Understanding the never-ending stream of encryption and decryption technology advancements is not often an in-house capability. The constant tug-of-war between organizations striving for data ethics and security versus hackers seeking to undermine existing shields will likely remain. However, any organization that has instituted at least some data security and ethics provisions is better positioned than businesses that make no effort. According to Harvard Business School, here are five principles of data ethics7 to apply at your organization.
Timing can be everything. A significant drawback of not having data ethics measures in place is that you might not be so effective retroactively if compromised. Additionally, consumer platform usage only covers how you can protect your data on software. Hardware is another matter, such as your computer’s hard drive, memory cards, USB disks, and other physical data-bearing devices.
 AVOIDING THE PITFALLS OF DIY DATA DESTRUCTION
AVOIDING THE PITFALLS OF DIY DATA DESTRUCTION
The average user wants to make sure data on an old device, perhaps private calls or emails does not fall into the wrong hands. How might some attempt to ensure data would not be accessible on a hardware device? For some – the answer is “old school.” Damage, crush, and discard the obsolete device. Break it down into tiny pieces so that no one can ever access it.
Unfortunately, that’s the exact method that criminals use when they’re trying to prevent their information from falling into the hands of the police. What’s more – it doesn’t work8. As technology has grown, the Mobile Forensics industry is constantly developing techniques to get “byte for byte” memory dumps of data off hardware devices.
Mobile forensics’ teams are using data retrieval techniques to uphold justice. Imagine the methods developed by hackers developing data retrieval techniques solely for black-market profit.
At the end of the day, one may have a destroyed device, which has done next to nothing to secure your data and instead has only served to exacerbate a growing problem of the proper disposal of electronic waste9, better known as e-waste.
DESTROYING DATA ETHICALLY AND FOR THE ENVIRONMENT
According to the UN Environment Program (UNEP), global e-waste, 20-50 million metric tons, continues to rise annually10. Electronics was considered “one of the fastest-growing waste components” in 2005, and its usage has only grown since then. As we continue using electronics in our daily lives and business, our awareness of how that impacts us is essential not to underestimate.
The problem of e-waste becomes a global concern when any improperly disposed electronics end up in our landfills, otherwise known as “toxic wastelands,” where heavy metals and chemicals seep into the soil, atmosphere, and water supply. This e-waste (referring to any electronic that has reached the end of its life cycle) has long-lasting implications for the future of our planet.
Guiyu, a city located in southeastern China, is known as the largest e-waste recycling site in the world. A study of its citizens noted11 an exhibition of “substantial digestive, neurological, respiratory, and bone problems,” with 80 percent of Guiyu’s children suffering from respiratory ailments. The e-waste created in Guiyu wasn’t a localized problem; instead, it grew exponentially. The United States is one of the largest generators of e-waste globally12, trailing only behind China.
While we’ve shined a light on why the average business owner might actively engage in destroying their electronics (convenience), the reality is that many people get rid of their electronics for much more mundane reasons. Screens crack, new versions are released, and hardware isn’t built to last13 like it once was. There are many reasons why business owners are engaging in creating e-waste. Becoming proactive about handling e-waste will only lead to benefit rather than harm.
DISPOSING OF HARDWARE DATA PROPERLY
There are two main benefits of certified disposal for your end-of-life electronics hardware, i.e., e-waste:
- To ensure that business and client data remains safe and is not accessible by nefarious third parties to be sold or abused, and
- To prevent the buildup of e-waste from damaging the environment around us.
The Research Ethics Board at Vancouver Island University14 has a good chart example guideline for getting rid of your data safely on a variety of mediums.
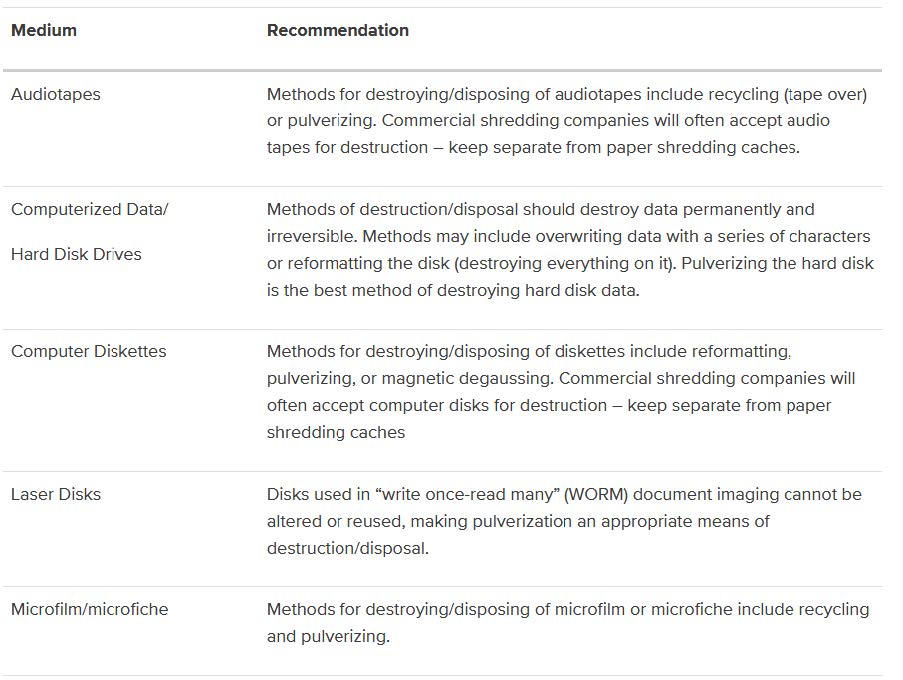
Each electronic medium has varying methods of data disposal. It can get more complex if you’re “cleaning house” or looking for a comprehensive solution.
At this point, business owners might consider recycling their e-waste. It is a tremendously viable option – companies that offer electronic recycling will disassemble, clean, and separate the materials. In 2012 the EPA noted that only 29 percent of the US’s e-waste was recycled, while the rest was “landfilled, incinerated, or stuck in a closet15.” However, with much of the recycled e-waste, another study16 revealed that developing countries received 40 percent by export, where recycling is typically unlicensed and unregulated. Thankfully, in the US, some electronics recyclers are dedicated to Zero Landfill Policies and no third-world exporting.

CONCLUSION
Your data and that of your customers are important, powerful, and highly sought after. We understand that the desire to ensure it is secured – and unusable by abusers might lead some to choose disposal methods that are more convenient and immediate but ineffective and harmful to the environment in the long run. The truth is there are ways to reconcile compliance and convenience – through responsible, ethical destruction of data by certified professionals17. Secure data destruction is obtainable by contacting local landfills and requesting certified e-waste drop-off locations or, for more prominent companies, by outsourcing to a firm dedicated to sustainability and green initiatives.
References
1. What is data ethics? https://royalsocietypublishing.org/doi/pdf/10.1098/rsta.2016.0360
2. We’re giving away more personal data than ever, despite growing risks. venturebeat.com/2019/02/24/were-giving-away-more-personal-data-than-ever-despite-growing-risks/
3. How many people use Google? https://www.semrush.com/blog/google-search-statistics/
4. Get a Summary of Data in Your Google Account https://support.google.com/accounts/answer/162744?hl=en
5. RiskBased Security 2020 Q3 Report https://pages.riskbasedsecurity.com/hubfs/Reports/2020/2020%20Q3%20Data%20Breach%20QuickView%20Report.pdf
6. 134 Cybersecurity Statistics and Trends for 2021 https://www.varonis.com/blog/cybersecurity-statistics
7. 5 Principles of Data Ethics for Business https://online.hbs.edu/blog/post/data-ethics
8. Burn, drown, or smash your phone: Forensics can extract data anyway https://www.zdnet.com/article/burn-drown-or-smash-your-phone-forensics-can-extract-data-anyway/
9. Cleaning Up Electronic Waste https://www.epa.gov/international-cooperation/cleaning-electronic-waste-e-waste
10. UN Report: Time to seize opportunity, tackle challenge of e-waste https://www.unep.org/news-and-stories/press-release/un-report-time-seize-opportunity-tackle-challenge-e-waste
11. Heavy metals concentrations of surface dust from e-waste recycling and its human health implications in southeast China https://pubmed.ncbi.nlm.nih.gov/18505015/
12. E-waste: An assessment of global production and environmental impacts https://pubmed.ncbi.nlm.nih.gov/19846207/
13. Design and Planned Obsolescence. Theories and Approaches for Designing Enabling Technologies. https://www.tandfonline.com/doi/pdf/10.1080/14606925.2017.1352879
14. Data Retention and Destruction (Chart, Page 4) https://research.viu.ca/research-ethics-board/data-retention-and-destruction
15. What Can We Do About the Growing E-waste Problem? https://news.climate.columbia.edu/2018/08/27/growing-e-waste-problem/
16. UN.org / III. Waste Management https://www.un.org/esa/dsd/resources/res_pdfs/publications/trends/trends_Chemicals_mining_transport_waste/ch4_waste_management.pdf
17. WELCOME TO R2v3, AN UPDATED R2 STANDARD FOR AN EVER-CHANGING WORLD https://sustainableelectronics.org/welcome-to-r2v3/
 Chiman Lee
Chiman LeeAs Director of Operations, Chiman Lee oversees Corporate eWaste Solutions (CEWS), Northern division’s corporate sales, marketing efforts, and business development. Chiman has helped triple the impact and capacity of CEWS since its founding, with over 70,000,000 lbs. of e-waste diverted from landfills. CEWS is a nationwide R2v3, CalRecycle, DTSC, and ISO-certified electronics reuse and recycling solutions provider. CEWS specializes in electronic asset recovery, data security, data and product destruction, e-waste recycling, plastic recycling, collection events, OEM RMA support, logistic support, regulatory reporting support, and social impact programs. Learn about our Zero Landfill Policy and more at cewsb2b.com